INTRODUCTION
CRYPTOGRAPHY the science of the enciphering and deciphering of messages in secret code or cipher
cryptography is used everywhere it protects money transfers and credit card numbers used over the internet
but its main purpose is to keep secret documents secure from foreign governments
TERMINOLOGY
CRYPTOGRAPHY the science of the enciphering and deciphering of messages in secret code or cipher.
PLAINTEXT the original message before encryption or after decryption
CIPHERTEXT The encrypted form of the PLAINTEXT
ENCRYPTION The process of converting the PLAINTEXT into a CIPHER.
DECRYPTION The process of converting the CIPHER back into PLAINTEXT.
CRYPTANALYSIS The science of recovering information from ciphers without knowledge of the key.
CRYPTOSYSTEM a system for encrypting information.
KEY The secret information known only to the transmitter and the receiver which is used to encrypt and decrypt the message
HISTORY
cryptology has been used to conceal information in writing since writing was first developed, Egyptians are the first knowN to used CRYPTOGRAPHY.
Early Greeks also used cryptology, they wrapped a piece of cloth around a baton called a scytale and wrote the message on it. When it was unwrapped it looked like decorations and was worn as a robe by a servant and delivered to the receiver. When it was wrapped again around a scytale the message was easily read.
Another Greek Polybius invented the Polybius checkerboard which was a 5 x 5 grid containing all the letters of the alphabet, each letter was converted into two numbers such as A becomes 11
-
1
2
3
4
5
1
A
B
C
D
E
2
F
G
H
I/J
K
3
L
M
N
O
P
4
Q
R
S
T
U
5
V
W
X
Y
Z
ex. CAR is 131142
later the the 19th C. cryptodevices were invented
they used mechanical rotors to scramble messages
most famous were the German Enigma and Japanese PURPLE used in WWII
todays ciphers are far more advanced than any before due to the aid of computers, which can compute extremely large numbers and use cryptosystems that are impossible with pencil and paper
SUBSTITUTION CIPHER
one of the more basic cipher is the substitution cipher
a unit of plaintext (usually letters or numbers) is replaced with other symbols or groups of symbols, the order is not changed ex. B becomes C, C - D and so on
one of the most well know is the Caesar cipher which A becomes D and so on
these are easily broken by studying the letter frequency
the Playfair cipher
on a 5 x 5 matrix similar to the Polybius checkerboard
a keyword is placed first then the remaining letters of the alphabet after it
there are many rules to substituting different letters from the plaintext into a ciphertext
Vigenère cipher
in its simpliest form a phrase or word is reapeated over and over and is the key.
the ciphertext letter is found at the intersection of the column of the plaintext letter and the row of the repeating key.
to decrypt the plaintext letter is found at the head of the column determined by the intersection of the diagonal containing the cipher letter and the row containing the key
Plaintext SAINT JOHN NEW BRUNSWICK
Key HALIF AXHA LIF HALIFAXHA
Ciphertext ZATVY JLON YMB IRFVXWFIK
TRANSPOSITION CIPHER
very simple route cipher is the rail fence which just staggers the letters between two rows
Plaintext SAINT JOHN NEW BRUNSWICK
Cytosystem S I T O N E B U S I K
A N J H N W R N W C
Ciphertext SITONEBUSIKANJHNWRNWC
ciphertext is gotten by writing the letters down from each column following the order in which each letters in the key appear in the alphabet
this plaintext now becomes INUKJWWZTESZNNNZSOBIAHRC
PRODUCT CIPHER
letters of the plaintext are made into several letters on the ciphertext
one of the more well known Product Cipher was the ADFGVX Cipher used by the German Army during WWI
it is a fractional cipher
it used a 6 x 6 matrix to substitution-encrypt the 26 letters of the alphabet and 10 digits into pairs of the symbols A, D, F, G, V and X.
a keyword is chosen and then the rest of the matrix is filled in with the alphabet and 10 digits
Ex. The keyword is "subject"
Plaintext S E N D H E L P
Ciphertext AA AV FV DF DX AV FF GA
this ciphertext is then run through a transposition cipher
O
R
A
N
G
E
5
6
1
4
3
2
A
A
A
V
F
V
D
F
D
X
A
V
F
F
G
A
Z
Z
the final cipher is now ADGVVZFAZVXAADFAFF
BLOCK CIPHERS
are what are used for modern encryption
translates blocks of plaintext (usually only 64 bit ) into ciphertext using a key and reversed when receiving the message
block size is becoming 128 bit due to faster processors
the iterated block cipher encrypts the same way only uses more stages
the more times this step is done the more secure the cipher is but it takes much longer to decipher
- DES
DES or Data Encryption Standard was up until a few years ago used to encrypt government documents
DES is symmetrical so both sender and receiver need the key
uses a 56 bit key to encode the data and is a friestal cipher which is very similar to a iterated cipher
the key is generated at random for each message from 72 quadrillion possibilities
a bit is a single unit of binary code either a 0 or a 1
there are over 72 quadrillion 56 bit combinations so chances of breaking it are remote
to break DES it would take 2^55 steps on average
DES was broken in 1997 by 16,000 computers running all the possible key until finally it was found after 18 quadrillion possibilities
Triple DES is now used which is DES done three times more until AES is completed
KEY DISTRIBUTION PROBLEM
there is a problem with these single key ciphers in that each member need a key to communicate with the next member
the equation is [n(n-1)]/2 so with 1000 members [1000(1000-1)]/2 = 499500
so this system becomes very impractical quickly
SOLUTION
the solution is a two key system or public key
with this the public key is used to encrypt and private to decrypt
now for a 1000 members there only needs to be 2000 keys 1000 public and 1000 private
up until 1976 a one key or symmetric system was used, the two key or asymmetric system is a relatively new invention as one key has been used for thousands of years
CRYTPANALYSIS
is the process of breaking a enciphered text
cryptanalysis is vital in wars most notably in WWII where the breaking of the Enigma and PURPLE ciphers was crutial in the winning of the war
the cryptanalysis of Enigma and PURPLE are one of the most celebrated triumphs of cryptanalysis
cIPHERTEXT ONLY ATTACKS
BRUTE FORCE ATTACK
an attack requires a lot of computing power and time to run
is basically just trying all the possibilities in a somewhat organized manner until the right one is found
this is a very impractical due to the large number of possibilities, such as DES which has 72 quadrillion
DICTIONARY ATTACK
this is a type of Brute Force Attack
essentially is running through all the words in a dictionary in hopes that the key is one of them
often uses for finding password because people often use easy to remember words as their passwords
PLAINTEXT ONLY ATTACK
PLAINTEXT ONLY ATTACKS ARE WHERE THE PLAINTEXT IS KNOWN AND IT CIPHERED VERSION AND YOU TRY TO FIND THE KEY
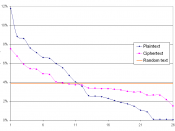
FREQUENCY TABLES
with single key cryptography usually some part of the original plaintext structure remains
for example with monoalphabetic substitution where plaintext letters are always replaced by different but always the same letters in the ciphertext ex. E will always be W in the ciphertext and so on
with a paragraph of jarbled letters there is a letter frequency which is how many times letters occur in that paragraph
in the normal English language there is a letter frequency, E occurs the most and has a frequency of .127 and T the next with .097
knowing this the letter frequencys can be overlapped for instance in this paragraph if W occurs the most then its most likely E and if F is the next then it is T