Synopsis
The Information system has unleashed countless opportunities for Industrial growth, activity, new applications, laborsaving accomplishments, improving the quality of decisions and many others. At the same time, Information technology has spawned a whole new field of crime and generated a series of problems for both designers and users of information systems. One of the problems is the crime from misusing of information system.
In the meanwhile, robust economic growth carries with it the potential for corruption. Evidence that this potential has become reality for many businesses can be found in a 2004 survey by the Computer Security Institute, which showed that 56% of businesses reported some form of unauthorized use of their information system. The same technology that is driving greater productivity is also facilitating large-scale financial fraud. The increasing number of technologically skilled individuals accessing a company's computer system increases the system's vulnerability to attack from within and without.
After the using computerized accounting information systems in both large and small businesses, higher efficiency and accuracy have brought to businesses. However, by misusing vulnerabilities through the accounting information systems for criminal purposes will make businesses suffer great losses and dangers.
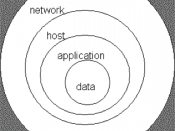
The vulnerability of information system
As systems became more complex and sophisticated, so did the problems of data integrity. Resource-sharing systems achieve their greatest advantage when used simultaneously by many customers. This also means simultaneous processing of data with varying needs for privacy. As the flexibility and capability of systems improve, the need for and the complexity of security controls threaten to grow at a faster rate. With many users on line at one time, system crashes become more serious and the entire operation becomes more complex, therefore subject to error. Finally, with the integration of data bases and the advent of data base management systems, the...