ARP Poisoning
Main Issues:
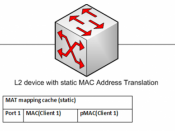
The Address Resolution Protocol's uses in detecting and rerouting traffic can cause havoc on a network where ARP's functionality is needed. ARP's capability of altering ARP tables at the switch makes it a prime target for hackers as point of entry in their attack. Because ARP works at both the network layer and the data link layer it can shutdown a network's data transfer with the outside world by confusing computers in understanding exactly where to pass information to.
Conclusions of the article:
ARP Spoofing is one of the most useful techniques of gaining access to protected material on a network that most hackers employ. It gives them full control over the data as it passes between the target and a gateway. Stopping ARP poisoning by disallowing it's functionality is a double edged sword in that it would stop the network from functioning in an efficient manner, because each time the target computer would have to request the MAC address of the other computer for each data transfer and authenticate it, which would cause major overhead.
Data is only as safe as the administrator's skill in providing protection and disabling services that causes such attacks to occur within a network.
My comments:
I personally enjoyed the article for it showed me just how powerful ARP is and also extended my learning learned in class of this utility and brought its importance to the forefront. Although I knew that the ARP utility was important I didn't know exactly that if it were not part of the TCP/IP protocol suite that the internet and networks will all crawl to a standstill. We used this utility in class but didn't change the individual mac addresses on the ARP table for each computer, but this article gave me hands on...


Hmmmm.....
this is still not helping
1 out of 2 people found this comment useful.