Steganography in Greek means covered or secret writing and is a long practiced form of hiding information. (Westphal, 2003)Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step farther by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it contains encrypted data.
As I mention before: Steganography is the process of hiding a message, while cryptography is the process of hiding its meaning. Examples of both are given with information on how the codes are used, and how they were broken. The main example is Mary Queen of Scot's code, the weakness of which led to her execution.
Steganography was used as recently as 2001 as told by the U.S. officials. They say that hidden in the pictures on several Web sites and the posted comments on sports chat rooms may lie the encrypted blueprints of the next terrorist attack against the United States or its allies.
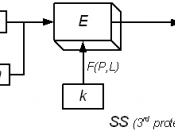
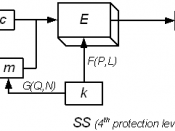
Steganography includes a vast array of techniques for hiding messages in a variety of media like text, images, sound. In text, messages hidden in the form of particular indentation like line shifting, vertical spacing etc. (Kessler, 2001)Type of Steganography:1- In text:- Line-Shifting Coding: The text lines are vertically shifted to encode the document uniquely. If a document is marked with line-shift coding, it is particularly difficult to remove the encoding if the document is in paper format. (Kessler, 2001)- Word-Shift Coding: In word shifting coding, code words are coded into a document by shifting the horizontal locations of words within text lines, while maintaining a natural spacing appearance.
Using the Alternate Methods: 1- Syntactic methods; 2- Semantic methods2- In images:To hide data in images,