ChekMate is a small business that specializes in check authorization at the point of sale. Currently, ChekMate consists of two remote offices and one main office. As the demand for point of sale check authorization increases to reduce fraud and identity theft, ChekMate needs a network design that will accommodate expansion.
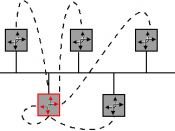
ChekMate will use a star topology in order to take advantage of the entire network not being affected if there is a problem with one of the hubs. However, when a hub is affected all computers and devices attached to the hub will be inoperable, but the entire network will not be affected. Although the costs of the cabling that is required can be high when using this topology, the manageability of this topology is well worth the cost.
ChekMate has also chosen to use a leased-line such as an Integrated Services Digital Network to provide a private network between the main office and the remote offices.
ChekMate will also make use of a mixed virtual private network. Using a mixed virtual private network will allow all of the virtual private network processes to be outsourced to an internet service provider. Having a virtual private network will allow ChekMate to connect all of the remote offices and the main offices together. Virtual private networks can also allow ChekMate employee's to work from remote locations such as one's home or hotel room if the employee is traveling.
The network protocols that will be used in ChekMate's network design include internet protocols, layer two tunneling protocols and layer three tunneling protocols. Internet protocols will be used when information is being transmitted through the LAN and WAN. Layer two protocols are used when both ends of the tunnel must agree to a communication session and all other configuration such as encryption, heading...